Most WordPress sites run an average of 20 plugins, yet many administrators miss critical threats hiding in plain sight. Understanding how plugin detection works can mean the difference between a safe website and a ticking security time bomb. This guide unpacks the real methods behind plugin detection, exposes common myths, and lays out practical insights for keeping your site secure and high-performing.
Plugin Detection Defined and Common Misconceptions
Plugin detection represents the systematic process of identifying and analyzing software extensions installed on a WordPress website, revealing critical insights about site functionality, security, and technological infrastructure. The technique goes beyond simple identification by providing deep forensic analysis of plugin characteristics, usage patterns, and potential vulnerabilities.
The research from Usenix introduces sophisticated detection methodologies like YODA, which examines plugin metadata and code structures to uncover potential security risks. These advanced techniques help WordPress site administrators understand exactly what plugins are running and assess their potential impact.
Common misconceptions about plugin detection include:
- All plugins are safe: Many administrators assume installed plugins are automatically secure
- Detection is simple: Identifying plugins involves more than surface-level scanning
- Manual checks are sufficient: Automated tools provide more comprehensive insights
Understanding plugin detection requires recognizing its multifaceted nature. It isn’t just about listing installed extensions but comprehensively analyzing their code signatures, update frequencies, security ratings, and potential interaction risks. Arxiv research emphasizes that accurate plugin detection is crucial for preventing potential security breaches, especially in complex WordPress environments where multiple plugins interact simultaneously.
Effective plugin detection helps website owners:
- Identify potentially vulnerable extensions
- Understand site technology stack
- Perform security audits
- Optimize website performance
For a comprehensive understanding of plugin detection strategies, check out our why use plugin detection tools guide.
Types of Plugin Detection Methods Explained
Plugin detection methods represent sophisticated technical approaches designed to identify and analyze software extensions within WordPress environments. These methodologies range from simple surface-level scans to advanced forensic analysis techniques that provide comprehensive insights into plugin characteristics and potential vulnerabilities.
Research from Arxiv highlights advanced detection techniques like μVulDeePecker, a deep learning-based system for multiclass vulnerability detection. This demonstrates the evolution of plugin detection from basic identification to complex vulnerability assessment, showcasing how technology has transformed our understanding of software extension analysis.
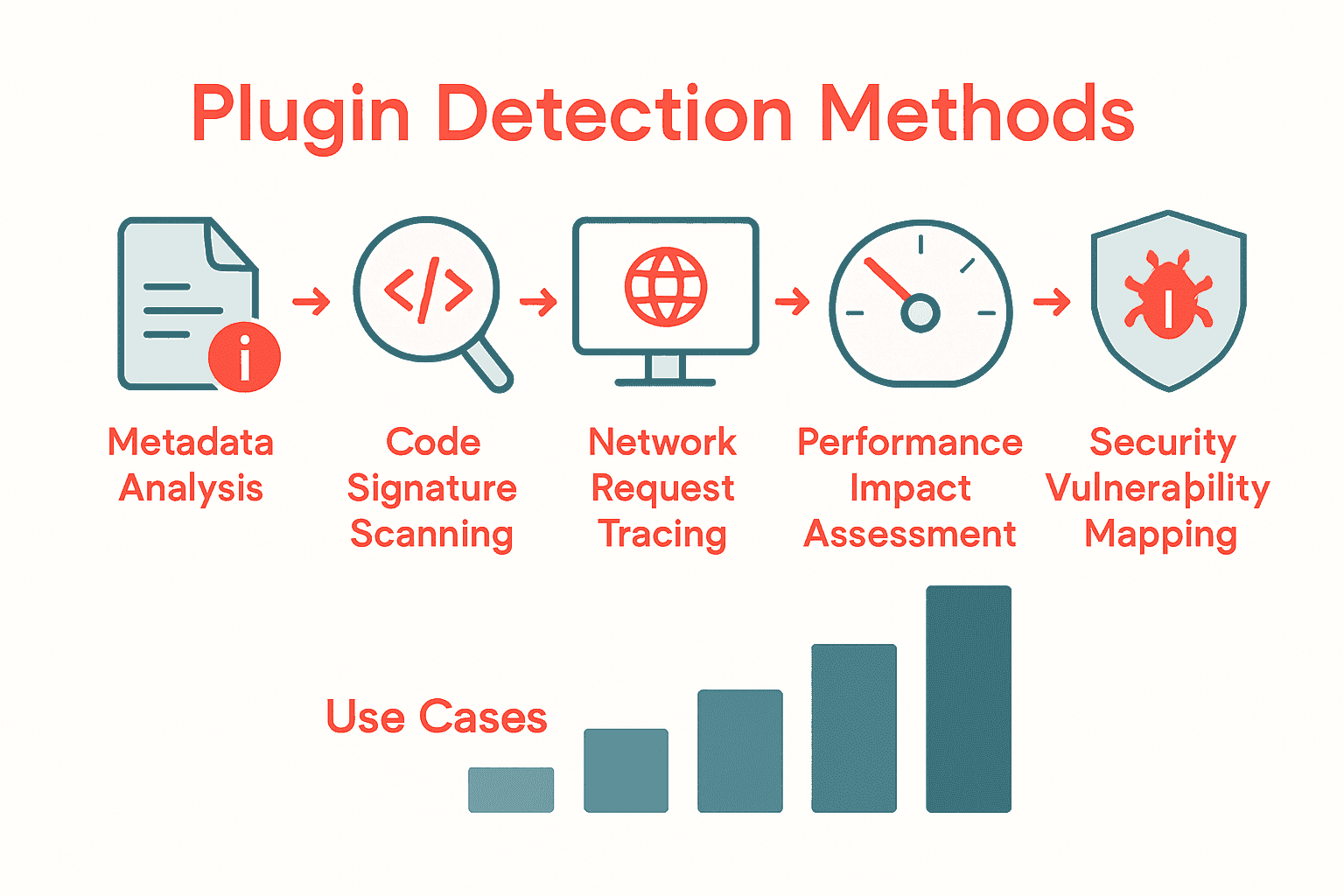
Key plugin detection methods include:
Here’s a comparison of key plugin detection methods and their main characteristics:
| Method | Description | Typical Use Case |
|---|---|---|
| Metadata Analysis | Scans plugin headers and config files | Basic identification Compliance |
| Code Signature Scanning | Detects unique code patterns and structures | Security auditing Vulnerability checks |
| Network Request Tracing | Monitors outgoing and incoming network connections | Detecting malicious activity |
| Performance Impact Assessment | Measures resource and performance metrics | Performance optimization |
| Security Vulnerability Mapping | Maps known vulnerabilities | Risk mitigation Patch planning |
- Metadata Analysis: Examining plugin headers, readme files, and configuration data
- Code Signature Scanning: Identifying unique code patterns and structures
- Network Request Tracing: Monitoring plugin network interactions
- Performance Impact Assessment: Measuring plugin resource consumption
- Security Vulnerability Mapping: Detecting potential security risks
The Arxiv research on VulDeeLocator further emphasizes the importance of fine-grained vulnerability detection, introducing deep learning techniques that can precisely locate and identify potential security weaknesses within plugin architectures.
Website administrators can leverage these detection methods to:
- Understand comprehensive plugin ecosystem
- Mitigate potential security risks
- Optimize website performance
- Make informed technology stack decisions
For a deeper exploration of WordPress plugin detection techniques, check out our comprehensive WordPress plugin detector guide.
How Plugin Detection Works Technically
Plugin detection operates through a complex, multi-layered technical process that goes far beyond simple file scanning. This intricate methodology involves sophisticated algorithms designed to comprehensively analyze WordPress plugin architectures, revealing deep insights into their functionality, security, and potential vulnerabilities.
Research from Usenix highlights the YODA tool, which demonstrates advanced plugin detection by meticulously parsing metadata and performing granular code analysis. This approach allows for precise identification of plugin roots, associated files, and potential security risks embedded within WordPress extensions.
The technical workflow of plugin detection typically involves several critical stages:
- File System Exploration: Scanning WordPress directories for plugin-related files
- Metadata Extraction: Parsing plugin header information and configuration data
- Signature Analysis: Identifying unique code patterns and structural characteristics
- Dependency Mapping: Tracking inter-plugin relationships and potential conflicts
- Performance Profiling: Evaluating resource consumption and execution patterns
Additionally, Arxiv research on Dev-Assist introduces multi-label machine learning techniques for detecting security-relevant methods within plugin code. This advanced approach enables more nuanced and intelligent plugin analysis, moving beyond traditional static detection methods.
Technical mechanisms for plugin detection include:
- Static code analysis
- Dynamic runtime inspection
- Network behavior monitoring
- Cryptographic signature verification
- Machine learning-based anomaly detection
Key Uses in WordPress Ecosystem and Industry
Plugin detection has become a critical strategic tool transforming how businesses, developers, and marketers understand and leverage WordPress technologies. This sophisticated approach provides unprecedented insights into website architectures, enabling more informed decision-making across multiple professional domains.
Research from Usenix highlights the YODA tool, which plays a crucial role in identifying malicious plugins within WordPress marketplaces. This demonstrates how plugin detection serves as a fundamental security mechanism, protecting websites from potential vulnerabilities and unauthorized extensions.
Key uses of plugin detection across the WordPress ecosystem include:
- Security Auditing: Identifying potential security risks and vulnerabilities
- Competitive Intelligence: Analyzing competitor website technologies
- Performance Optimization: Detecting resource-intensive plugins
- Compliance Monitoring: Ensuring plugins meet regulatory standards
- Market Research: Understanding technology adoption trends
The WordPress Device Detector exemplifies practical plugin detection, showcasing how these tools can enhance user experience by providing deep analytics about site visitors and their technological environments. This approach transforms raw data into actionable business intelligence.
Industry professionals leverage plugin detection for multiple strategic purposes:
- Cybersecurity risk assessment
- Technology stack analysis
- Digital marketing intelligence
- Website performance benchmarking
- Competitive landscape mapping
Explore the latest WordPress plugin trends with our comprehensive industry guide.
Risks, Privacy, and Legal Considerations
Plugin detection introduces complex legal and ethical challenges that extend far beyond simple technological implementation. Website owners and developers must navigate a nuanced landscape of privacy regulations, security protocols, and potential legal liabilities when analyzing WordPress plugin ecosystems.
Research from Usenix emphasizes the critical risks associated with malicious plugins, highlighting the urgent need for robust detection methods that protect user privacy and maintain legal compliance. This research underscores the importance of proactive plugin analysis in safeguarding digital infrastructure.
Key privacy and legal risks in plugin detection include:
- Data Collection Limitations: Ensuring minimal personal information exposure
- Consent Requirements: Obtaining user permissions for detailed plugin scanning
- Intellectual Property Concerns: Respecting plugin developers’ code ownership
- Cross-Border Regulatory Compliance: Navigating international privacy laws
- Potential Liability for Security Breaches: Understanding legal responsibilities
Arxiv research on Dev-Assist demonstrates advanced approaches to addressing privacy concerns, introducing sophisticated methods for detecting security-relevant code while minimizing intrusive data collection. These techniques represent a critical evolution in responsible plugin analysis.
Practical steps for mitigating legal and privacy risks involve:
- Implementing transparent scanning methodologies
- Developing clear user consent protocols
- Maintaining strict data anonymization practices
- Regularly updating privacy impact assessments
- Consulting legal experts specializing in technology law
Learn more about navigating WordPress plugin legal landscapes in our comprehensive guide.
Take Control of Your WordPress Plugin Landscape Today
Understanding what plugins are running on your WordPress site is essential to maintaining security, optimizing performance, and staying ahead of potential vulnerabilities. If you have ever worried about hidden risks or struggled to map out your site’s plugin ecosystem, you are not alone. Many site owners miss out on the deep insights that come from precise plugin detection as described in the article.
Discover how WPoptic can transform your approach by providing detailed data on plugin usage and site configurations. Our platform lets you perform advanced competitive analysis, monitor security threats, and create targeted lead lists based on real plugin insights. Don’t wait until vulnerabilities or performance issues affect your site. Explore real-time plugin detection with WPoptic Lead List and empower your development and marketing strategies today. For a deeper dive into how plugin detection benefits your WordPress ecosystem, check out our comprehensive guide and unlock new intelligence for your business.
Frequently Asked Questions
What is plugin detection in WordPress?
Plugin detection refers to the systematic process of identifying and analyzing software extensions installed on a WordPress website, providing insights into site functionality, security, and technological infrastructure.
Why is plugin detection important for website security?
Plugin detection is crucial for security because it helps identify potentially vulnerable extensions, enables security audits, and assesses the risks associated with installed plugins, thereby preventing security breaches.
What are the common methods used for plugin detection?
Common methods for plugin detection include metadata analysis, code signature scanning, network request tracing, security vulnerability mapping, and performance impact assessment, each providing different insights into plugin characteristics and risks.
How does plugin detection work technically?
Plugin detection typically involves stages such as file system exploration, metadata extraction, signature analysis, dependency mapping, and performance profiling, utilizing advanced algorithms to analyze plugin architectures comprehensively.
Recommended
- Why Use Plugin Detection Tools: Complete Guide – WPoptic
- WordPress Plugin Detector Test 2025: What Plugins Is This Site Using? – WPoptic
- Complete Guide to WordPress Plugin Trends – WPoptic
- How to Analyze WordPress Sites for Plugins and Themes – WPoptic
- Automotive Diagnostic Process for Diesel Injection Pros – My WordPress
- 7 Essential Security WordPress Tips You Must Know in 2025 – WPCTO